Google Cloud Stack Pre-Settings
Google Cloud Stack Pre-Settings
Create Google Cloud service account and create a key DR purpose
Create a Google Cloud service account and create service account key with correspinding permissions, detail requirement please refer to below document. And create a service account key of service account for setup.
Create a service account
Tips
Reference to Google Cloud official Create a service account documentation
In the Google Cloud console, go to the Create service account page.
Select a Google Cloud project.
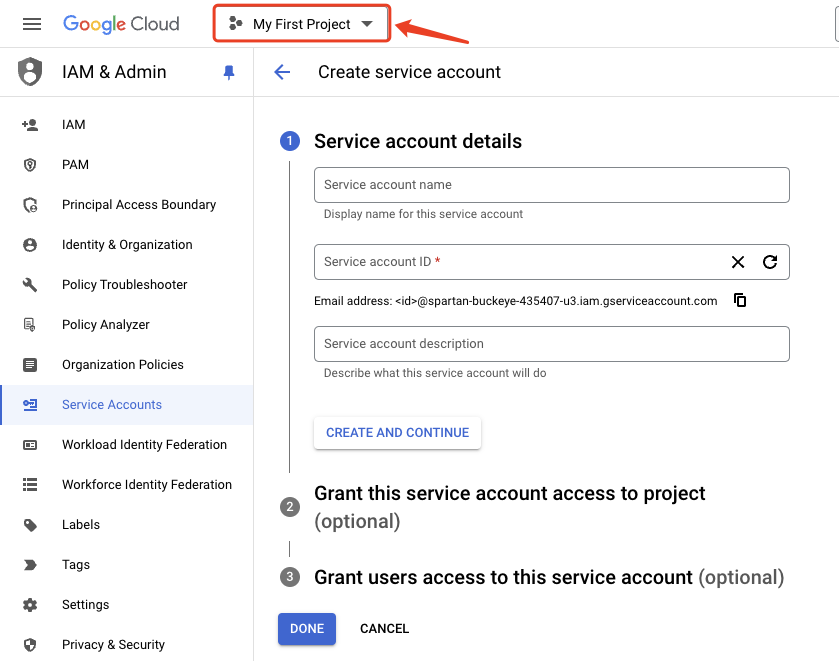
- Enter a Service account name to display in the Google Cloud console
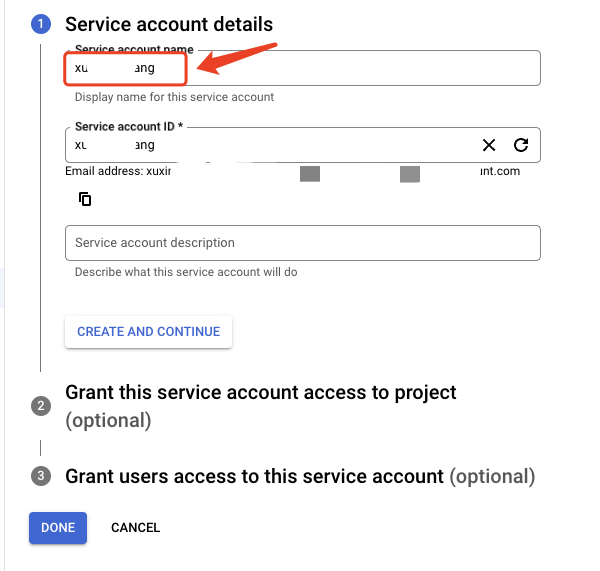
The Google Cloud console generates a service account ID based on this name. Edit the ID if necessary. You cannot change the ID later.
Optional: Enter a description of the service account.
Set access controls now, click CREATE AND CONTINUE and continue to the next step.
Select a role menu, Quick access > Basic > Roles, then click Editor.
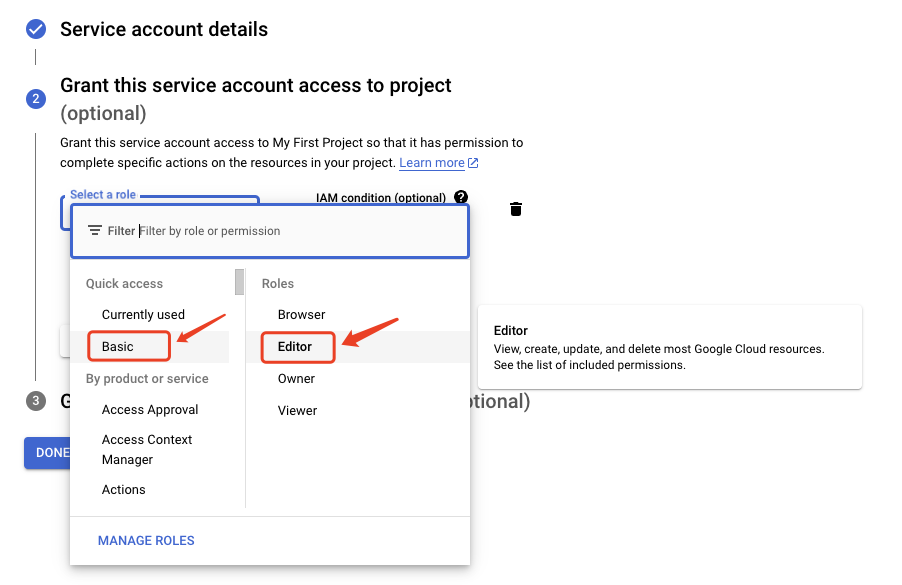
When you are done adding roles, click CONTINUE.
Click Done to finish creating the service account.
Create a service account key
Tips
Reference to Google Cloud official Create a service account key documentation
In the Google Cloud console, go to the Service accounts page.
Select a project.
Click the email address of the service account that you want to create a key for.
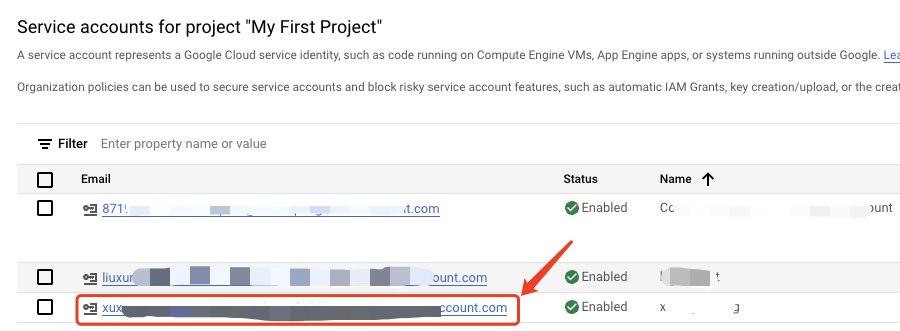
- Click the KEYS tab.
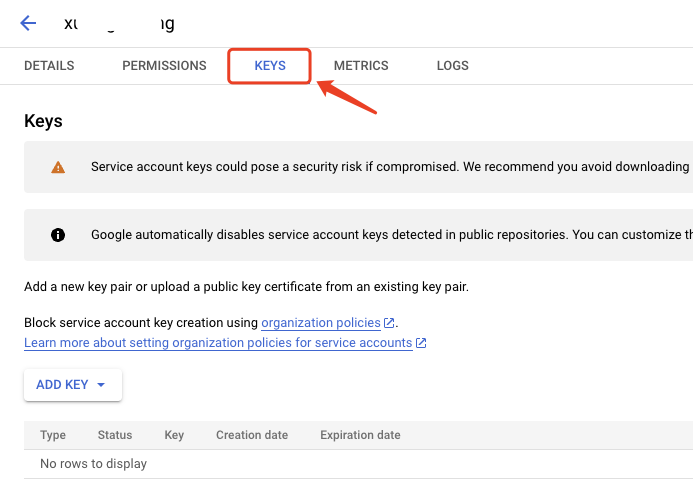
Click the ADD KEY drop-down menu, then select Create new key.
Select JSON as the Key type and click CREATE.

Clicking CREATE downloads a service account key file. After you download the key file, you cannot download it again.
The downloaded key has the following format, where PRIVATE_KEY is the private portion of the public/private key pair:
{
"type": "service_account",
"project_id": "PROJECT_ID",
"private_key_id": "KEY_ID",
"private_key": "-----BEGIN PRIVATE KEY-----\nPRIVATE_KEY\n-----END PRIVATE KEY-----\n",
"client_email": "SERVICE_ACCOUNT_EMAIL",
"client_id": "CLIENT_ID",
"auth_uri": "https://accounts.google.com/o/oauth2/auth",
"token_uri": "https://accounts.google.com/o/oauth2/token",
"auth_provider_x509_cert_url": "https://www.googleapis.com/oauth2/v1/certs",
"client_x509_cert_url": "https://www.googleapis.com/robot/v1/metadata/x509/SERVICE_ACCOUNT_EMAIL"
}open it and locate the value of private_key and copy it.
Obtain Google Cloud Platform Credentials information
When targeting the Google Cloud, the following authentication information of the Goole Cloud platform is required to complete the authentication docking of the API interface.
How to obtain Google Cloud Platform Credentials information?
Create VPC & Subnet
Tips
Reference to Google Cloud official Create auto network documentation
Reference document for disaster recovery network planning overview architecture
Create VPC Network and Subnet According to Google Cloud Documentation. Explanation: Establish your network based on the following disaster recovery network scenarios.
- Intranet VPN Access:
If accessing through an intranet VPN, create a DR VPC network and place HyperBDR ECS instances in this network.
- Disaster Recovery VPC:
Dedicated VPC network and subnet for HyperBDR disaster recovery and backup, interconnected with the on-premises IDC through VPN.
- Business VPC:
Business VPC network and subnet used for disaster takeover and drills.
Create VPC Firewalls for HyperBDR or Cloud Sync Gateway
Open policies required for HyperBDR & Cloud Sync Gateway: What port strategies should be opened for HyperBDR and Cloud Sync Gateway?
Tips
Reference to Google Cloud official Create VPC firewall rules documentation
- Login to the VPC networks, click you want used the VPC Name
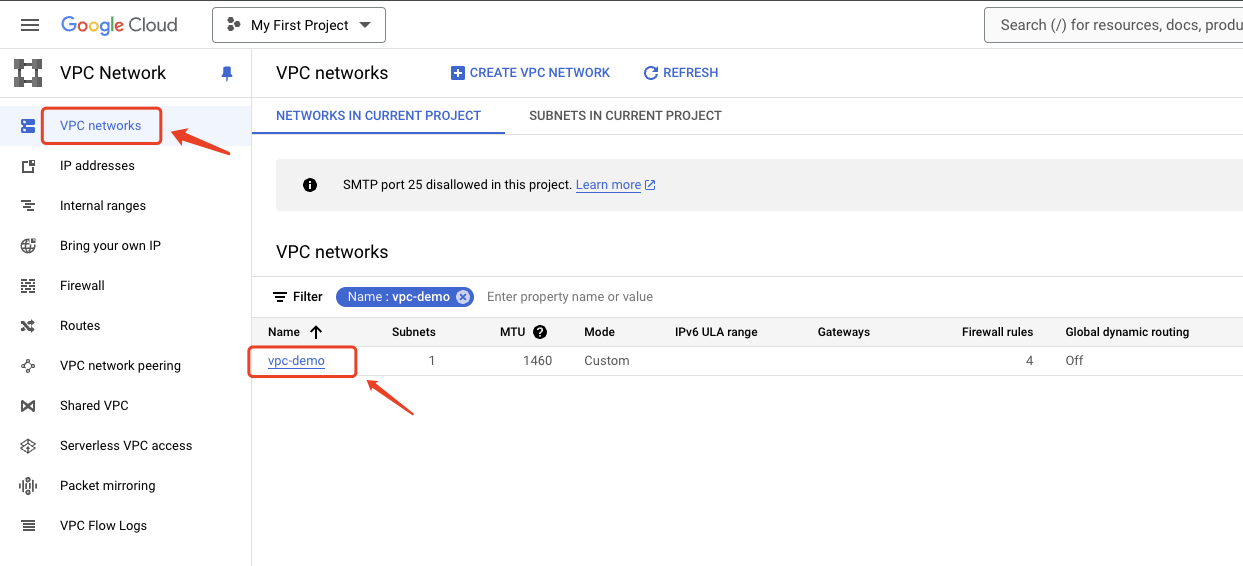
- Click the FIREWALLS top menu, and click ADD FIREWALL RULE button
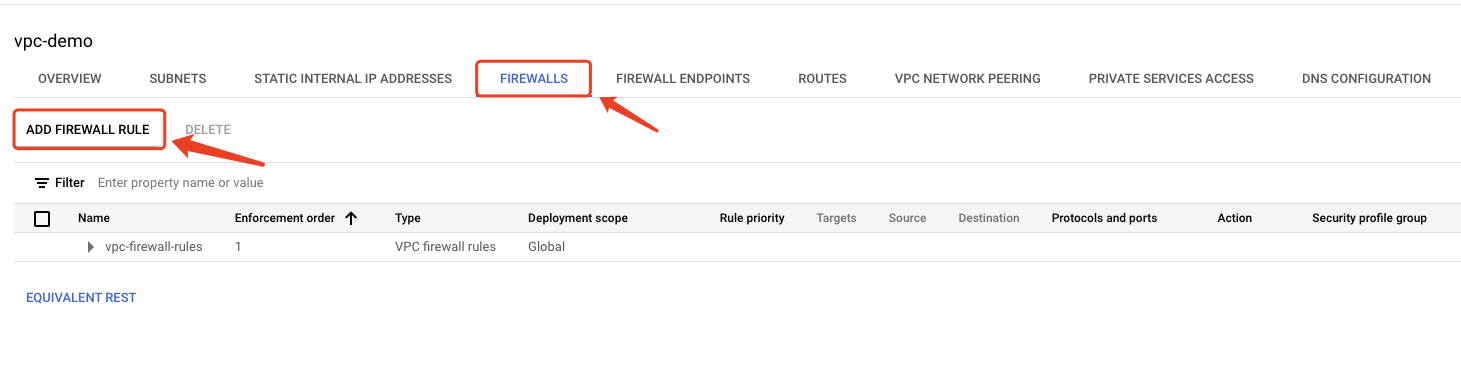
Configure according to the open policy list. For specific configuration steps, refer to the official documentation.
Configure disaster recovery drill network policy
For specific network policy requirements, please refer to the How to configure a disaster recovery network policy? documentation.
Tips
Reference to Google Cloud official Peer two VPC networks documentation